
The Use Case for a Jump Server
What is a jump server?
A jump server, also known as a bastion host, or jump host, serves as an intermediary server that allows secure access to other servers within a hosted environment. HorizonIQ can provide an additional server to be used as a jump server as part of your environment. It’s usually a simple, low-cost server and can yield some good benefits for you to manage your environment.
What can a jump server be used for?
A jump server can be used for secure system administrator access to the servers in an environment. To accomplish that, the system administrator uses multi/two-factor authentication on an SSL VPN connection to the firewall— which upon successful authentication—provides access to the jump server. The access to the jump server can be SSH for Linux or Remote Desktop Protocol (RDP) in the case of Windows. From the jump server, the system administrator can connect over a private network to any of the hosts that they need to do work on.
All the remaining servers that are used for production will have extremely limited public access, if at all. For example, the web server might be the only server that the firewall allows public access to, and even then, it will be limited to http (port 80) and https (port 443). This limits the attack surface to the servers in the production environment.
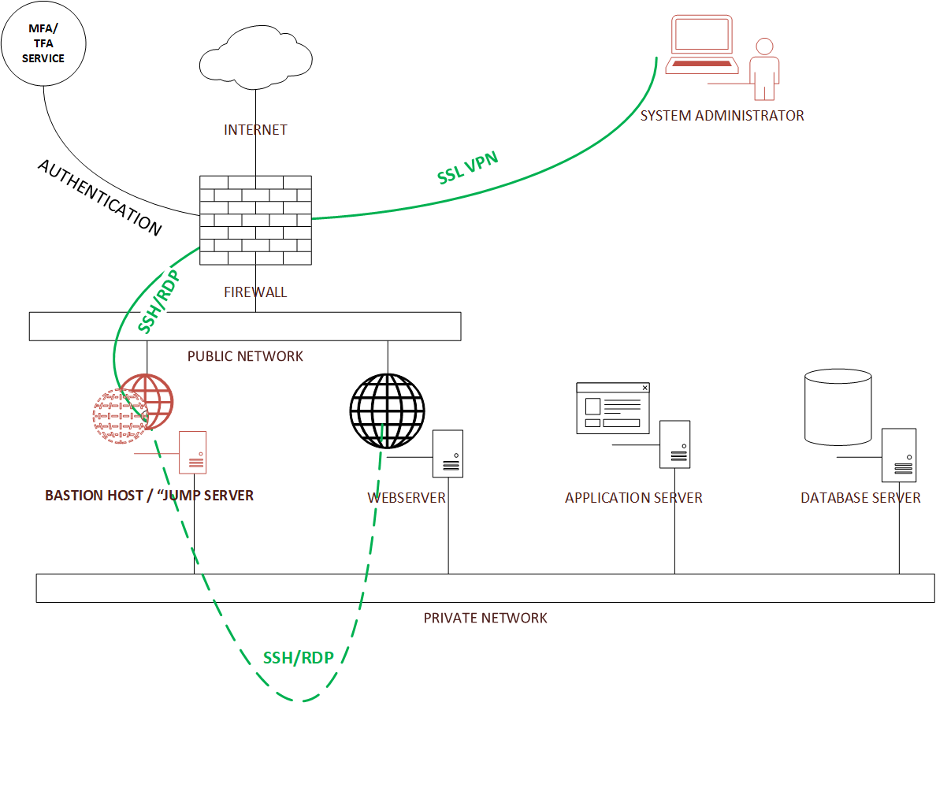
That said, the jump server needs to be kept up to date, locked down, and frequently patched. I would even go as far as using the Defense Information Systems Agency (DISA) issued Security Technical Implementation Guides (STIG) for the Operating System used for the jump server.
Where can I find jump server tools and administration?
A useful website for this is sigviewer.com/stigs and just search for your operating system and applications. Stigviewer also categorizes each finding with an ID and is classified by severity level. You can open Finding IDs for all of the “high” and “medium” findings, and it gives details on the finding and “Fix Test” on how to remedy the finding. This could also prove useful in an audit since you can point to your use of DISA STIGs, and document any exceptions by Finding ID numbers.
Do I need additional jump server resources?
Jump servers do not typically need a great deal of resources. If the jump server is used for other tasks like patching, backup, monitoring, etc. then it may need additional resources.
Once the jump server is in place, it can also be used for other useful system administration tasks. Let’s explore some of these:
Security:
a. Access Control: A jump server acts as a single-entry point, enforcing strict access controls. Only authorized users can connect to the jump server, reducing the attack surface compared to allowing direct access to every server in the network.
b. Authentication: Users must authenticate themselves to the jump server before gaining access to other servers. This adds an extra layer of security and helps prevent unauthorized access.
Network Segmentation:
a. Isolation: The jump server creates a separation between the internal network and external connections. This isolation helps contain and mitigate the impact of security incidents, limiting the exposure of internal servers.
Audit and Monitoring:
a. Logging: All access to servers can be logged on the jump server, providing an audit trail for security and compliance purposes. This centralized logging makes it easier to monitor and review user activities.
b. Monitoring Tools: Security monitoring tools can be deployed on the jump server to detect and respond to suspicious activities, providing an additional layer of protection.
Simplified Firewall Configuration:
a. Firewall Rules: Instead of configuring complex firewall rules for each internal server, administrators can focus on securing access to the jump server. This simplifies the overall firewall configuration and reduces the likelihood of misconfigurations.
Identity and Access Management:
a. Single Sign-On (SSO): Integrating the jump server with identity and access management systems allows for centralized user management and authentication. Users can often use their existing credentials to access the jump server.
Secure File Transfer:
a. File Copy: Instead of copying files directly to internal servers, users can first copy files to the jump server and then transfer them internally. This helps prevent malicious files from entering the internal network.
Proxy for External Access:
a. Remote Access: In scenarios where administrators need to access servers from external networks, the jump server can act as a proxy, providing a secure point of entry. This is particularly useful for remote administration.
Software Update Management:
a. Centralized Updates: Software updates and patches can be applied to the jump server first, and then extended to the internal servers. This ensures a controlled and consistent update process.
Disaster Recovery:
a. Backup Configuration: The jump server can be a part of the disaster recovery plan. In the event of a security incident or system failure, administrators can focus on restoring the jump server and then proceed to recover other servers.
Can a jump server help my business?
A jump server enhances security, simplifies administration, and provides a controlled and monitored gateway for accessing servers in a hosted environment. Its implementation is a common best practice in securing network infrastructures. Be sure to speak your HorizonIQ account team about adding a jump server to your environment to benefit from these advantages.



